
Recent trends
- The amount of spam in email traffic decreased by 2.2% compared to November’s figure. The overall average being 82.6% for December.
- Links to phishing sites were found in 0.84% of all emails, a decrease of 0.13% compared to November.
- Malicious files were found in 0.16% of all emails, a decrease of 0.67% compared with the previous month.
- The amount of fraudulent spam has increased considerably.
- Fraudsters continue to use “wavy” pictures with background noise to bypass filtering.
Spam in mail traffic
The amount of spam detected in mail traffic averaged 82.6% in December 2009. A low of 78.2% was recorded on 25 December with a peak of 88.9% on 27 December.
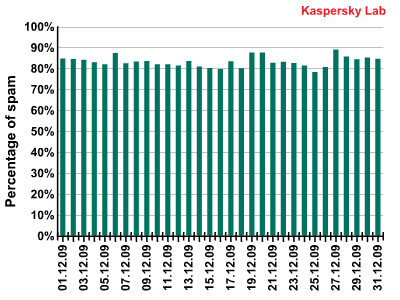
Percentage of spam in mail traffic in December 2009 (1-26 December)
Malware in mail traffic
Malicious files were found in 0.16% of all emails, a decrease of 0.67% compared with the previous month which means that the amount of emails containing malicious files reached the same level as spring-summer 2009.
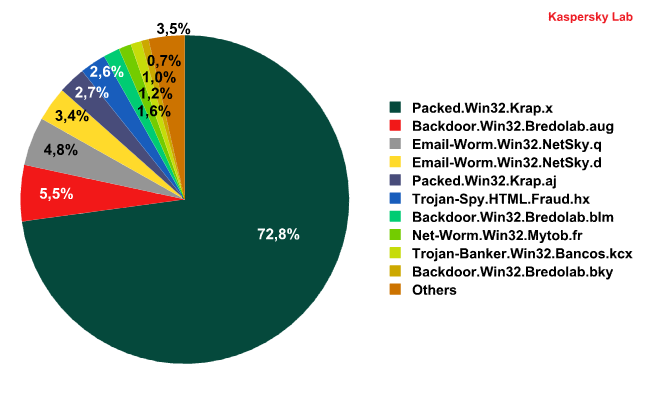
Malware found in spam messages during December 2009
In December, the absolute majority of malicious messages contained files packed with the help of Packed.Win32.Krap.x. As a rule, this Krap modification is used for packing Zbot, FraudTools and Iksmas. Nearly 73% of all the malware contained in emails was detected as Packed.Win32.Krap.x.
Another Krap modification – Packed.Win32.Krap.aj – was also among the top ten most widespread malicious programs. Files that had been packed with it were found in 2.7% of all spam messages. For example, Packed.Win32.Krap.aj was found in a mass mailing allegedly sent by Facebook. We have already received similar messages which contained different modifications of this packer.
Malware found in spam messages during December 2009
Compared to the leader, the share of the other top 10 entries was not that impressive. Though Backdoor.Win32.Bredolab was represented with three modifications – Backdoor.Win32.Bredolab.aug, Backdoor.Win32.Bredolab.blm and Backdoor.Win32.Bredolab.bky – it still could not muster a combined total of more than 8%. To recap, Backdoor.Win32.Bredolab is a Trojan program from a backdoor family. When the Trojan is launched it incorporates your computer into a botnet. Having requested data from the command centre, a malicious program then downloads additional modules from the global network. These modules are either fake antivirus programs that find hundreds of non-existent malicious programs and ask for money to treat them, or spyware that steals user passwords. November’s top 10 contained a significant number of malicious programs from this family.
In December, the top 10 saw the return of Email-Worm.Win32.NetSky. It was last on top back in August 2009. In December modifications of this worm (Email-Worm.Win32.NetSky.q and Email-Worm.Win32.NetSky.d) occupied third and fourth places respectively. Email-Worm.Win32.NetSky spreads across the Internet in the form of an email attachment. It is sent to all the email addresses found on an infected computer. The worm activates when a user launches an infected file (by double clicking on the attachment). The worm then installs itself on the new system and repeats its distribution procedure.
An interesting newcomer in December was Trojan-Banker.Win32.Bancos.kcx., a Trojan program that affected 1.04% of all infected email traffic. It is designed to steal passwords for the WebMoney service.
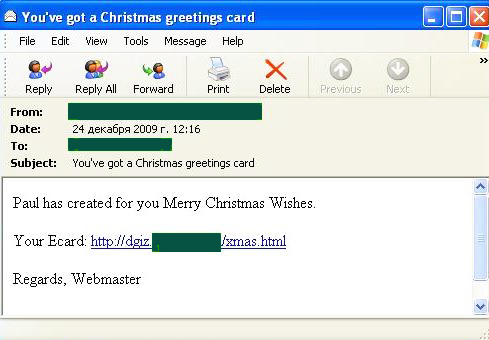
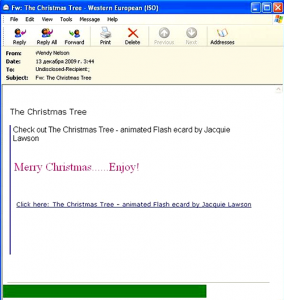
In December, we also recorded an interesting Christmas mass mailing which distributed malicious programs with the help of a malicious link:
Users found Christmas greetings in the message which contained a link to the following e-card:

While unsuspecting users were reading the card, Trojan-Downloader.JS.Shadraem.a was downloading to their computer.
These particular mass mailings were mentioned in our November spam report where we warned users of emails with links to e-cards that download malicious programs to their computers.
Phishing
In December 2009, PayPal (-8.84%) and eBay (-1.99%) remained the most popular targets for phishers. The social networking site Facebook came third, suffering 1% more phishing attacks than the previous month.
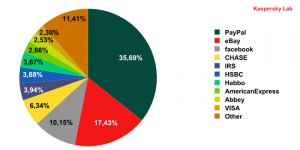
Organizations targeted by phishing attacks in December 2009
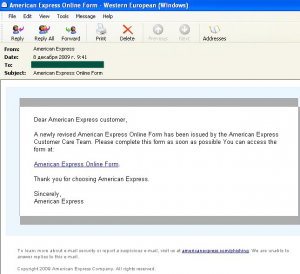
The number of attacks targeting the IRS halved compared to the previous month, while VISA and American Express entered the phishers’ favorite top ten targets. This was quite logical – during the Christmas festivities it is much easier to scare a user with the prospect of their credit card being blocked than with a reminder about unpaid taxes.
The messages that users received resembled official notifications from legitimate organizations, but actually contained links to phishing sites.
Organizations targeted by phishing attacks in December 2009
In addition, HSBC bank, which moved down one position (-0.66%), was subjected to several serious attacks that involved social engineering techniques – a user was informed about an unauthorized payment made to their account. The message asked users to verify their account to confirm receipt of the payment. If users entered their credentials in the hope of a pre-Christmas windfall, they ended up playing into the hands of the phishers.
Phishers continue to pay a lot of attention to users with accounts for the popular online game World of Warсraft, so fans of this game should be wary of potential scams. The addresses and messages in the fraudulent emails are very similar to the real address and messages, but they only target user data.
Sources of spam
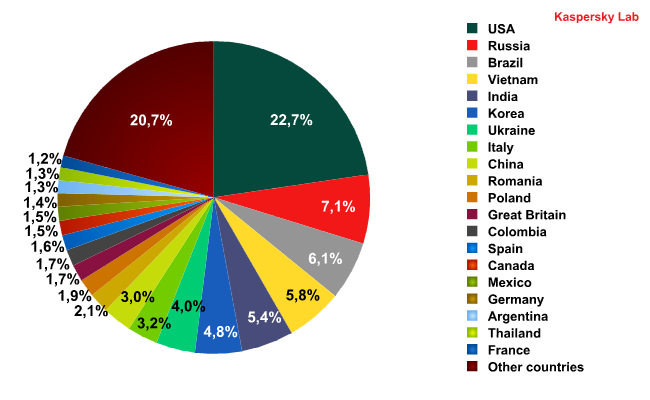
In December both leaders maintained their positions as the prime distributors of spam – the US with an increase of 3% compared to the previous month and Russia, though the quantity of spam originating from there decreased by 1% when compared to November. India fell from third to fifth, having distributed 1.3% less spam than in November. Brazil came third though the amount of spam coming from there remained largely unchanged (-0.16%). Fourth place was occupied by Vietnam with an increase of 1.05% compared to the previous month. Interestingly, Ukraine and China moved up to seventh and ninth places respectively with an average increase of 1% compared to November.
The UK distributed 1.72% of the spam in December, which is virtually the same as the previous month.
Spam by category
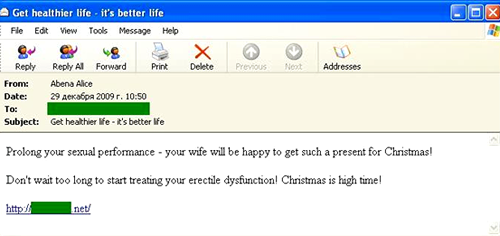
The Medications and health-related goods and services category retained the lead among English-language spam with over 35% of the total volume of spam. The Christmas theme was very popular, especially with spammers offering dubious pills for male impotency.
The link in the email leads to a site with a Christmas theme.
We expected December would see an increase in fraudulent activity related to the Christmas and New Year period, and we were not wrong – the amount of fraudulent spam increased by 5%. This meant the Computer fraud category overtook the Fake designer goods category to rate second in December’s top ten.
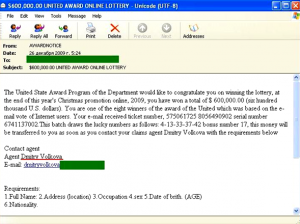
The fraudsters’ use of the Christmas theme seems to have affected the content of Nigerian letters and notifications of “lottery wins”. For example, in the email below a user is informed of a Christmas lottery win:
Interestingly, the “agent” in the “United States Award Program” is someone called “Dmitry Volkova” which sounds rather funny because Dmitry is a male name while the surname is distinctly female.
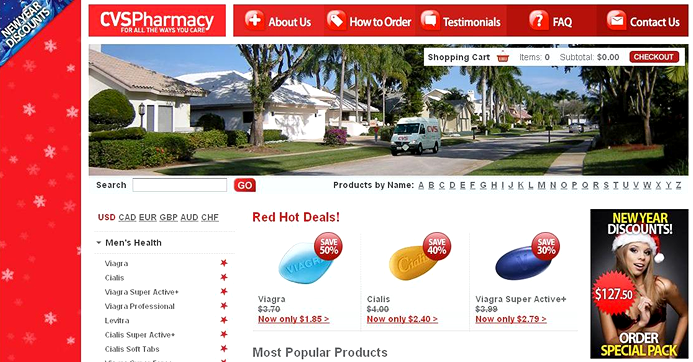
The amount of spam advertising fake designer goods decreased slightly compared to the previous month. Fraudsters tried to persuade users that the best Christmas present was a cheap Rolex replica.
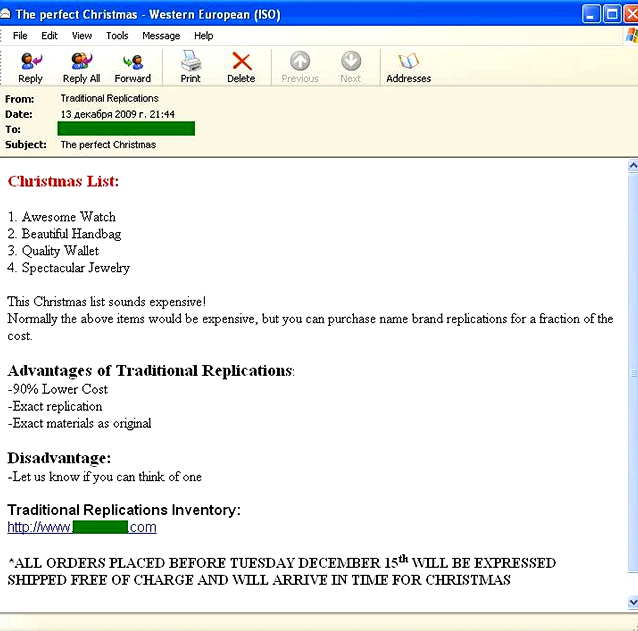
December saw a considerable increase (+5%) in the Other goods and services category. This was due mainly to advertisements for Christmas presents. For example, the following messages were very popular:
European spam emails advertising casinos and cheap software once again made their presence felt in the run-up to the winter holidays. It seems the spammers were certain that a glossy Christmas feel and attractive discounts would be a hit with users.
The quantity of Adult content spam increased slightly. Spammers were obviously working on the assumption that Christmas and New Year were not only family celebrations but also a time when lonely people felt even lonelier.
Spammer methods and tricks
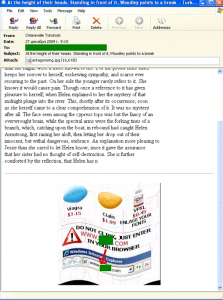
A particularly large mass mailing in December was noted for messages that combined several spammer tricks. First of all, the message included text containing random words and phrases. Secondly, the spam content contained in the picture was distorted using two “noise” methods – the background of the image was in the form of randomly chosen geometrical shapes and the image itself had a “wavy” form which varied in each message.
Conclusion
As expected, in December fraudsters used fake e-cards in order to make users download malicious programs. These “cards” were usually located on malicious web pages. Meanwhile, the quantity of spam with malicious attachments decreased considerably. We forecast that this trend will continue into January.
The percentage of phishing messages will stabilize for some time as of January, but this doesn’t mean that cybercriminals are likely to abandon this type of scam.























Spam evolution: December 2009